The Audit Trails page provides a comprehensive record of all changes made within your system. This chronological log helps you track who made changes, what was modified, and when these modifications occurred—essential for accountability, troubleshooting, and compliance.
What You Can Monitor
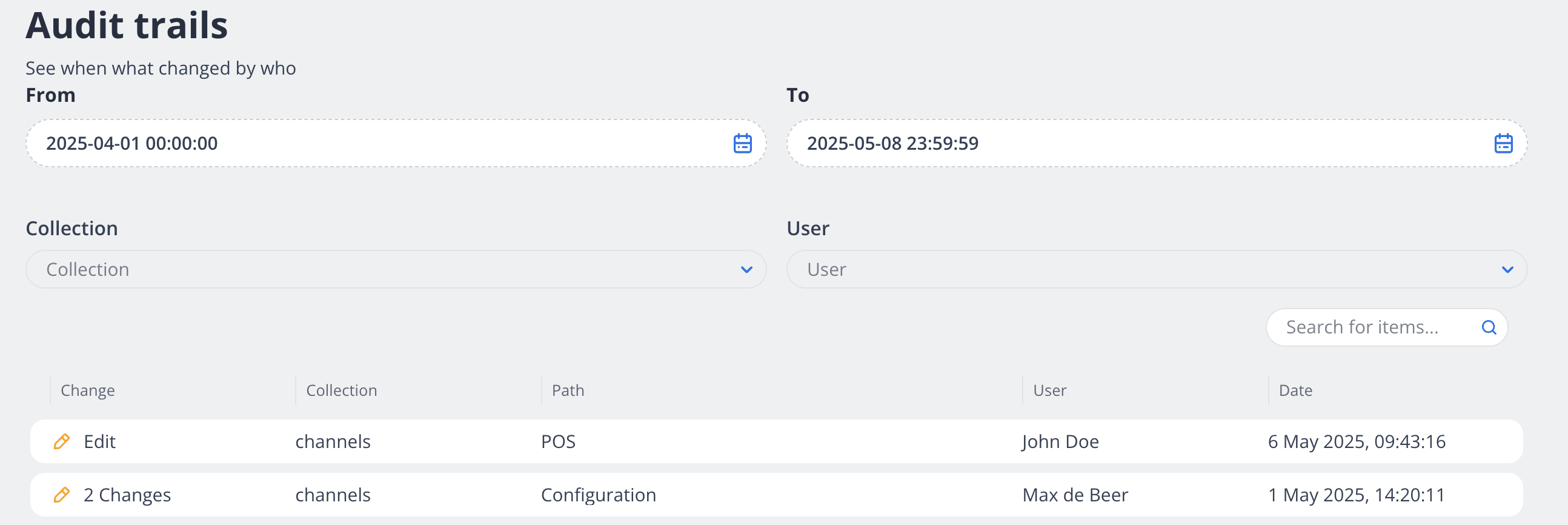
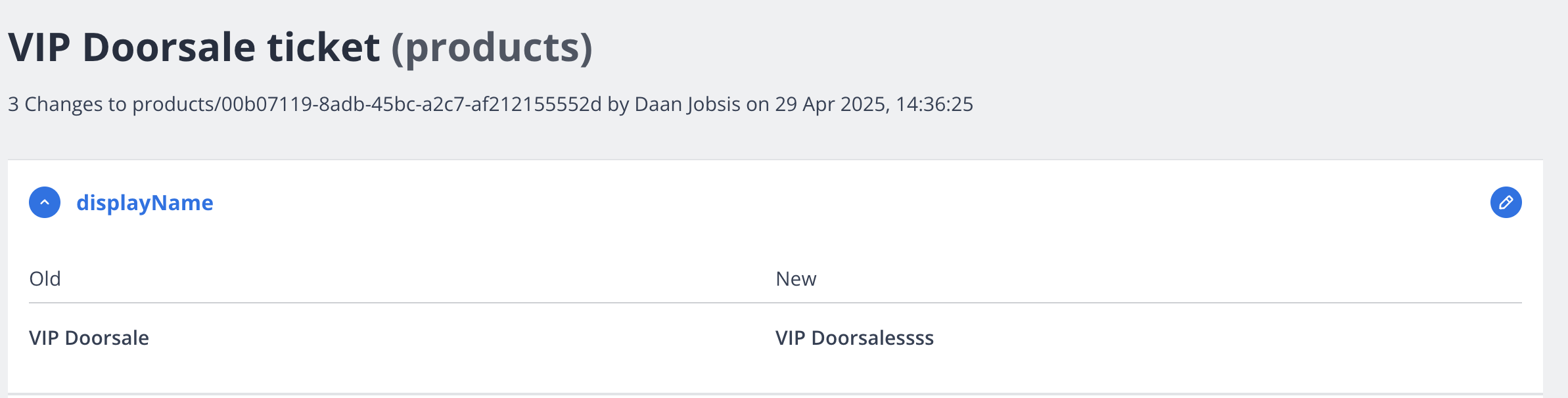
Change History
The audit trail displays a detailed record of all system modifications:
-
Change Type - Whether an item was added, edited, or removed
-
Collection - The category of data that was modified (channels, products, etc.)
-
Path - The specific location or identifier of the changed item
-
User - The name of the person who made the change
-
Date and Time - When the change occurred, shown in precise timestamp format
Filtering Options
At the top of the page, you can refine your view using filters:
-
Date Range - Set "From" and "To" dates to view changes within a specific period
-
Collection - Filter by data category (channels, products, users, etc.)
-
User - See changes made by a specific team member
How to Use Audit Trails
Daily Operations
-
Verify recent changes made by your team
-
Confirm that planned updates were properly implemented
-
Identify unexpected changes that might require attention
Troubleshooting
-
Track down when and how a specific issue was introduced
-
See which user made a particular change that might need correction
-
Review the sequence of changes leading up to a problem
Compliance and Security
-
Maintain records of all system modifications for regulatory requirements
-
Detect unauthorized changes or suspicious activity
-
Document who has accessed or modified sensitive information
Team Management
-
Monitor staff activity and engagement with the system
-
Identify users who might need additional training based on their changes
-
Verify that only authorized personnel are making changes to critical areas
The Audit Trails page is an essential tool for maintaining system integrity and accountability across your business operations. Regular review of this information helps ensure your system remains secure, properly configured, and compliant with your business policies.
